Artificial Intelligence
Hackers booby trap NPM with cross-language imposter packages
Rewrite the Hackers are abusing the Node Package Manager (NPM) registry — a database of JavaScript packages — to target...
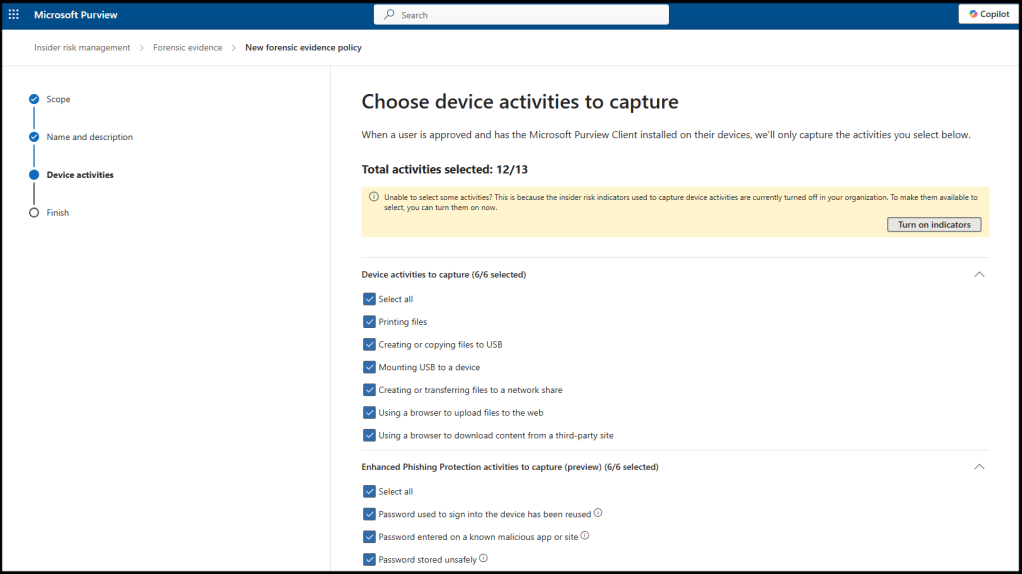
How to capture forensic evidence for Microsoft 365
Rewrite the Next you need to create your forensic evidence policies. In the Purview portal, go to “Forensic evidence policies”...
CrowdStrike cuts 500 jobs in AI pivot, but flags risks
Rewrite the Analysts and market trends suggest additional factors, such as economic uncertainties, including potential trade policy shifts and fluctuating...
„CISOs sprechen heute die Sprache des Business“
Rewrite the Godfrey: Ja, ich denke schon. Aber es hat auch viel damit zu tun, wie die CISOs heute auftreten....
What is CTEM? Continuous visibility for identifying real-time threats
Rewrite the What distinguishes CTEM from other methods? CTEM differs fundamentally from conventional security methods because risks are recognized and...
FBI warns that end of life devices are being actively targeted by threat actors
Rewrite the “If a business is using one of these routers, they’re setting themselves up for attacks on their infrastructure,”...