Rewrite the
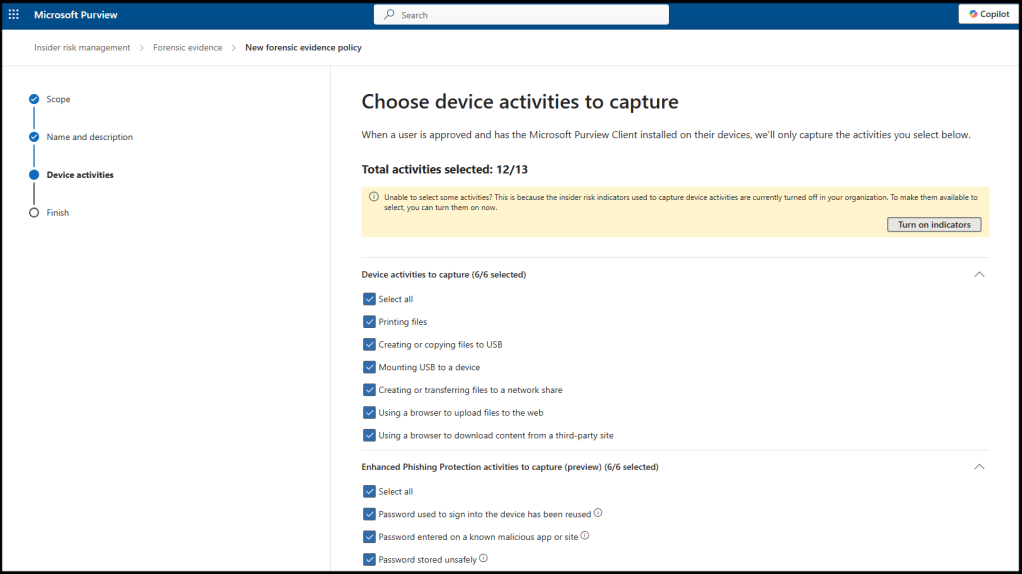
Next you need to create your forensic evidence policies. In the Purview portal, go to “Forensic evidence policies” and select “Create forensic evidence policy.” Specify which activities to capture, such as printing, file exfiltration, specific apps or websites, or all activities for selected users. “All activities” is not a typical setting and is used only for a set period during an investigation. You can also use Microsoft 365 Defender’s Advanced Hunting and Activity Log features for additional forensic analysis.
Susan Bradley / CSO
Caveats and limitations
Even with these settings, there can be times that you are at the mercy of the vendor. Forensic examinations of cloud assets can be complicated. Tracking through your log files to review what OAuth authentication was abused often takes expert review of these log files. In additional you don’t get memory dumps or full control like you do on endpoints. You often must open a support ticket with your vendor to request log files, thereby delaying your investigation and response.
There are also budget limitations to be aware of. For example, you may need to purchase additional storage to store the forensic evidence you wish to capture.
in well organized HTML format with all tags properly closed. Create appropriate headings and subheadings to organize the content. Ensure the rewritten content is approximately 1500 words. Do not include the title and images. please do not add any introductory text in start and any Note in the end explaining about what you have done or how you done it .i am directly publishing the output as article so please only give me rewritten content. At the end of the content, include a “Conclusion” section and a well-formatted “FAQs” section.